Types of Cyber Attacks That Can Hurt Your Company
It started innocently enough for Simon Bunce. In 1999, he applied for a credit card through a major supermarket. He began making benign purchases online for everyday things, like all of us.
Fast forward five years to 2004, when police surprised him at his home in the UK—with a search warrant. They handcuffed him and put him in jail.
Although he was innocent of any wrongdoing, he was accused of being a pedophile. His family disowned him, authorities seized his computers and drives, he lost his job, and his world became a living nightmare.
The real perpetrator was in Indonesia, over 7,000 miles away. He had stolen Bunce’s credit card info during a cyber attack on the supermarket, then used that info to purchase child pornography.
It’s one of the most chilling tales of identity theft imaginable and illustrates how cybercrime can go far beyond financial ruin.
Although there are many types of cyber attacks, the individual stories hit closest to home for most of us. But we should all think about business cyber threats because of the potential to expose large groups of people.
If you’re an owner, partner or other principal in a business, it can open you up to staggering liabilities. While this article only touches the surface, knowing where the risks lie is a crucial first step in preventing them.
In no particular order, here are five of the most common cyber attack examples:
1. Malware
One of the largest “categories” of cyber attacks is Malware. The simplest definition is malicious software that infects a computer, server or network—without the user’s knowledge.
It qualifies as its own category because there are so many forms it can take. It can self-deploy, replicate itself, hide, infect, disguise, and destroy. Some of those forms include the following:
Software or Macro Viruses. These viruses attach themselves to software applications, then replicate when the program starts, attaching to code elsewhere in the system.
Trojans. Like the hollow wooden horse used in Greek history, this malware looks like something it’s not, like a useful program. Inside, however, a sinister plot awaits to open a gate and allow the invaders to enter.
Worms. Have you ever heard of the planarium worm? It’s a flatworm that, when cut into pieces, each piece will completely regenerate into a whole worm. Unlike viruses, worms don’t attach to files. They are self-contained and propagate through email, creating copies and infecting entire systems.
Boot-Record Viruses. These viruses activate when a computer starts, load into memory, then begin infecting any connected computer or drive.
Ransomware. Almost a category all by itself, ransomware is one of the most dangerous types of malware. It ties up data and holds it hostage until you pay up. Ransomware can be especially devastating to a small business because it can stop you dead in your tracks.
According to Charlotte IT Solutions, there are multiple points of entry for ransomware. Businesses must use some of the most sophisticated IT security protocols available to stay safe.
2. Phishing Attacks
Phishing attacks are what they sound like—a bad guy putting some bait out there on a hook to see if you’ll bite. The bait looks like something you want or something you can trust.
One of the most common phishing attacks is an email designed to look like it’s from a trusted source—like your bank or credit card company. The goal is to get you to click on a link and “verify” (hand over) personal information. It’s often under the guise of some security threat that you need to address.
3. DOS/DDOS Attacks
Denial of Service or Distributed Denial of Service attacks are meant to create so much traffic on a server or website that it can’t function.
Imagine a congested highway in the city at rush hour. In the IT world, that’s what happens to your system in a DOS/DDOS attack. Sometimes hackers carry out these attacks for malice or revenge, but it also creates a perfect scenario to demand payment from the victim.
4. SQL Attacks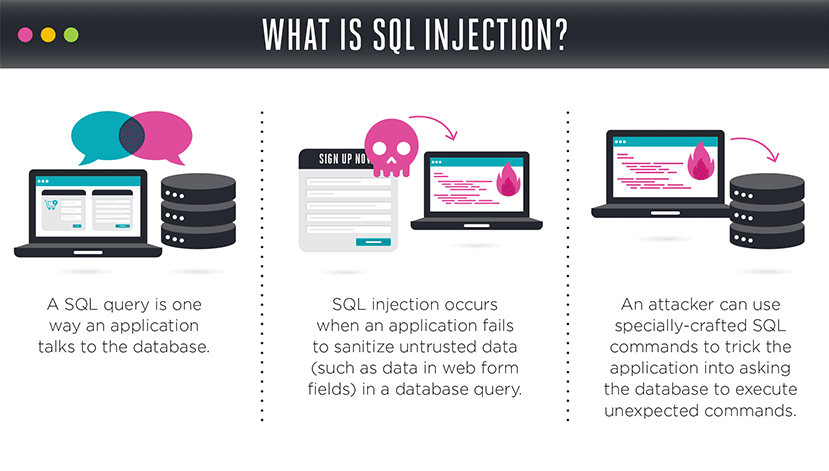
Pronounced “sequel,” SQL stands for Structured Query Language. An SQL attack is an attack on a database of records. Much like a master hypnotist, it asks innocent-sounding questions, or queries, to gain access to more information.
Every time you enter a username and password, the system “queries” a database to find a matching record, then lets you in if correct.
By exploiting weaknesses in computer language, hackers can get a system to return all records available in the database at once.
5. Passwords
It might surprise you to know that the average business employee has 191 passwords to keep track of. Let that sink in for a moment. Because the majority of people use the same or similar passwords everywhere, it’s not surprising that 81% of data breaches happen because of passwords.
The emerging use of two-factor authentication has helped to squelch the problem, but it’s still epidemic.
The Hidden Effects
Often, we think about cyber threats as financial, but the hidden costs are far-reaching.
Remember our innocent victim Simon Bunce? His story wasn’t about money at all, at least not in the beginning. But the dominoes fell about every direction they could.
To get an idea of the exponential effect of a business data breach, consider this: Over the next five years, 146 billion records will fall into the wrong hands.
That’s 20 times the world’s current population.
The other risks of cyber attacks on business include damage to reputation, lost customers, unrecoverable records, employee ID theft, and legal liability. The list goes on.
The Bottom Line
With so many types of cyber attacks on the rise, you can’t bury your head in the sand and expect to survive. You must first be able to recognize threats and be proactive—before something happens.
The first step in recognizing threats is security awareness training and should be a critical part of your overall security strategy.




















