Virtual Private Networks and Malicious Content
✨ Key Points
- Malicious and unauthorized content is widespread and often difficult to identify, which is why virtual private networks are commonly used to add an extra layer of online protection.
- Torrenting and file sharing can expose users to legal and security risks.
- Using a VPN helps protect privacy and reduce online threats while browsing or downloading.
The internet makes it incredibly easy to access and share content, but that convenience also comes with hidden risks.
Malicious files, unauthorized downloads, and unsafe websites are far more common than many users realize.
Often, people focus on getting the content they want without thinking about the legal, privacy, or security consequences.
One common example is torrenting.
While torrent technology itself isn’t illegal, a large portion of shared files are copyrighted or unsafe.
Downloading these files can expose users to legal trouble, malware, or unwanted tracking — even if it happens unintentionally.
Using a Virtual Private Network (VPN) adds an important layer of protection.
A virtual private network (VPN) helps keep your online activity private, reduces exposure to harmful content, and lowers the risk of your personal data being monitored or misused while browsing or downloading files.
In today’s online environment, where threats aren’t always obvious, taking steps to protect your connection isn’t about hiding it’s about staying secure, informed, and in control.
Each person can download it from https://www.bestvpnrating.com/best-vpn-torrenting to work with torrent files anonymously.
How to Work With VPNs
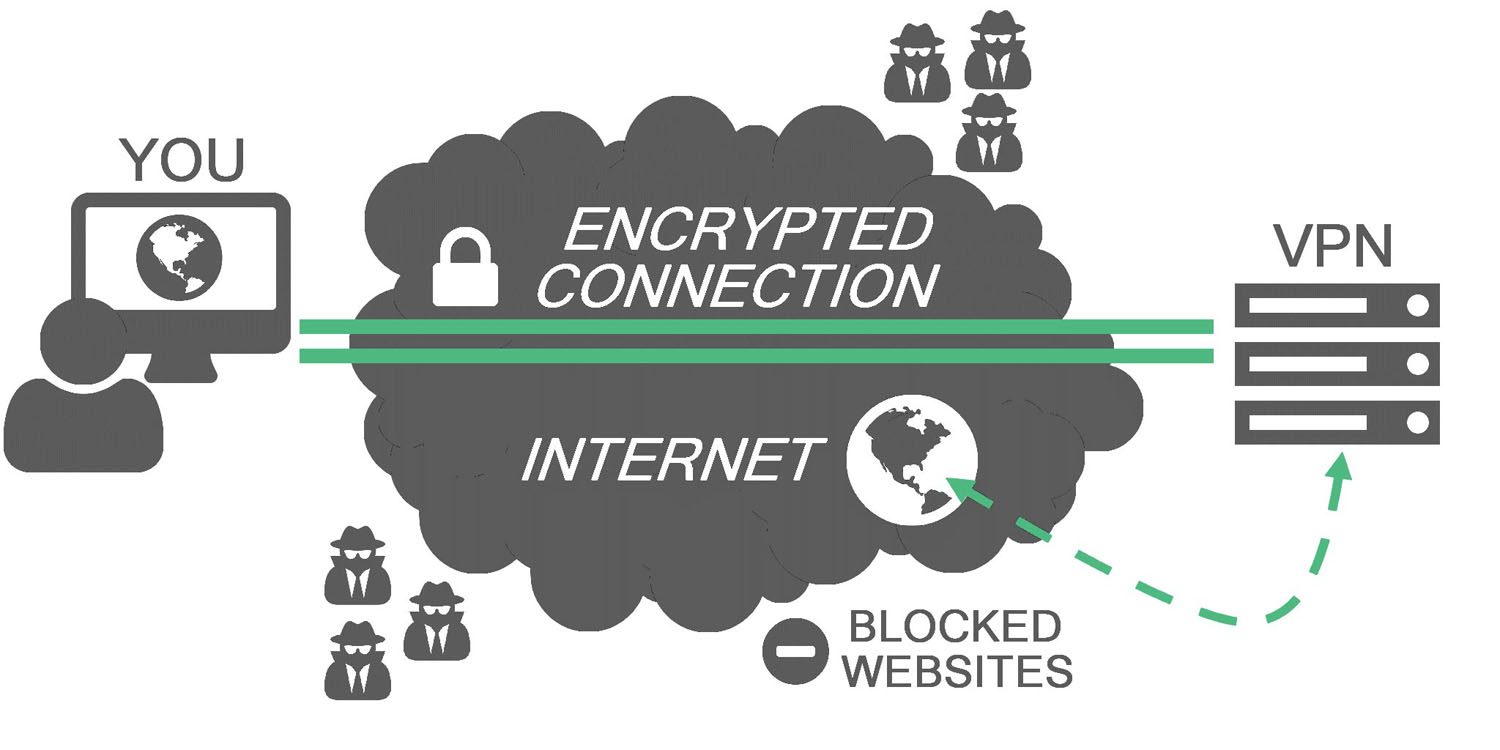
VPN technology is now widely used around the world because it helps people protect their privacy and secure their internet connection.
As more personal activity moves online, users want greater control over who can see their data and how it’s used.
A VPN works by masking your IP address and encrypting your connection.
This helps reduce exposure to tracking, unsecured networks, and certain online threats — especially when using public Wi-Fi or accessing sensitive accounts.
While virtual private networks don’t make all activity “invisible,” they do help keep your identity and browsing activity more private.
How to Get a VPN on Your Computer
Getting started with a VPN is simple:
Choose a trusted VPN provider. Look for well-reviewed services that clearly explain their privacy policy, security features, and limitations. Independent reviews and VPN comparison sites can help you make an informed choice.
Decide between free and paid options. Some free VPNs are suitable for basic use, while paid services often offer faster speeds, stronger security features, and more server locations. Choose based on your needs, not just price.
Download and install the software. Once installed, the VPN allows you to route your connection through servers in different regions, helping protect your data while browsing.
Change server locations if needed. Many VPNs offer multiple server options, which can improve connection reliability or help access region-specific services that are legally available to you.
Why People Use VPNs
VPNs are commonly used to:
Protect personal data on public or unsecured networks;
Reduce tracking by websites and advertisers;
Secure online activity when traveling or working remotely;
In some regions, access to certain online services may be limited.
VPNs can help users maintain privacy and connection security, but it’s important to follow local laws and service terms when using them. Get more info about this service.
Why Using a VPN While Torrenting Is Important
Torrenting involves sharing files with multiple users at the same time.
While the technology itself is widely used and legal in many cases, it also comes with privacy and security risks that many users overlook.
Because anyone can contribute files to a torrent, users may unknowingly connect to unsafe or unauthorized content.
This can expose personal information, browsing activity, or IP addresses to third parties — including trackers, advertisers, or malicious actors.
Using a VPN while torrenting helps reduce these risks by adding a layer of privacy and protection to your internet connection.
A VPN can help by:
Hiding your IP address, making your online activity less visible;
Encrypting your connection, so data can’t be easily intercepted;
Reducing exposure to tracking and monitoring during file sharing.
With encryption in place, your internet traffic is far more difficult for outsiders to read or misuse.
Even users with advanced technical skills would struggle to access personal data sent through a properly secured VPN connection.
As online privacy concerns continue to grow, more users are choosing VPNs as a practical way to stay secure and protect their personal information while browsing, streaming, or downloading content.